
Useful
21.12.2022
Distributed denial of service attacks are gaining more and more popularity on the Internet. Such type of attacks aim at the exhaustion of technological resources in various layers of traditional network communication models. The most common target of attack is the organization’s corporate structure, as a group of compromised devices coordinately send illegitimate requests to the final destination. In this way, the goal is to exhaust the system resources of the organization's key equipment or to flood the network.
Having extensive experience and detailed statistics, network specialists from Evolink annually perform a detailed analysis of the most common attacks, new trends, as well as interesting facts about one of the most common hacker attacks, namely DDoS.
All statistics in this document are solely from Evolink's monitoring and protection systems and concern the Internet traffic of the company's customers for the period December 2021 - November 2022.
The year in brief:
The total volume of malicious traffic filtered by Evolink's Anti-DDoS security platforms for the past 12 months is measured in Petabytes (1 Petabyte = 1000 Terabytes). The peak capacity of illegitimate packets during the attack was reported to be 36.3 Gbps. By comparison, standard Internet service today is usually between 100 and 1000 Mbps. An attack of this volume can repeatedly flood the network and system resources of the infrastructure.
|
Attack Type |
Number |
Percentage |
|
DNS Size Abnormal |
22667 |
41% |
|
Location Attack |
21492 |
39% |
|
ACK Flood |
41544 |
7% |
|
UDP Flood |
1038 |
2% |
|
FIN/RST Flood |
832 |
2% |
|
HTTPS Flood |
676 |
1% |
|
Global TCP Abnormal |
575 |
1% |
|
DNS Format Error |
551 |
1% |
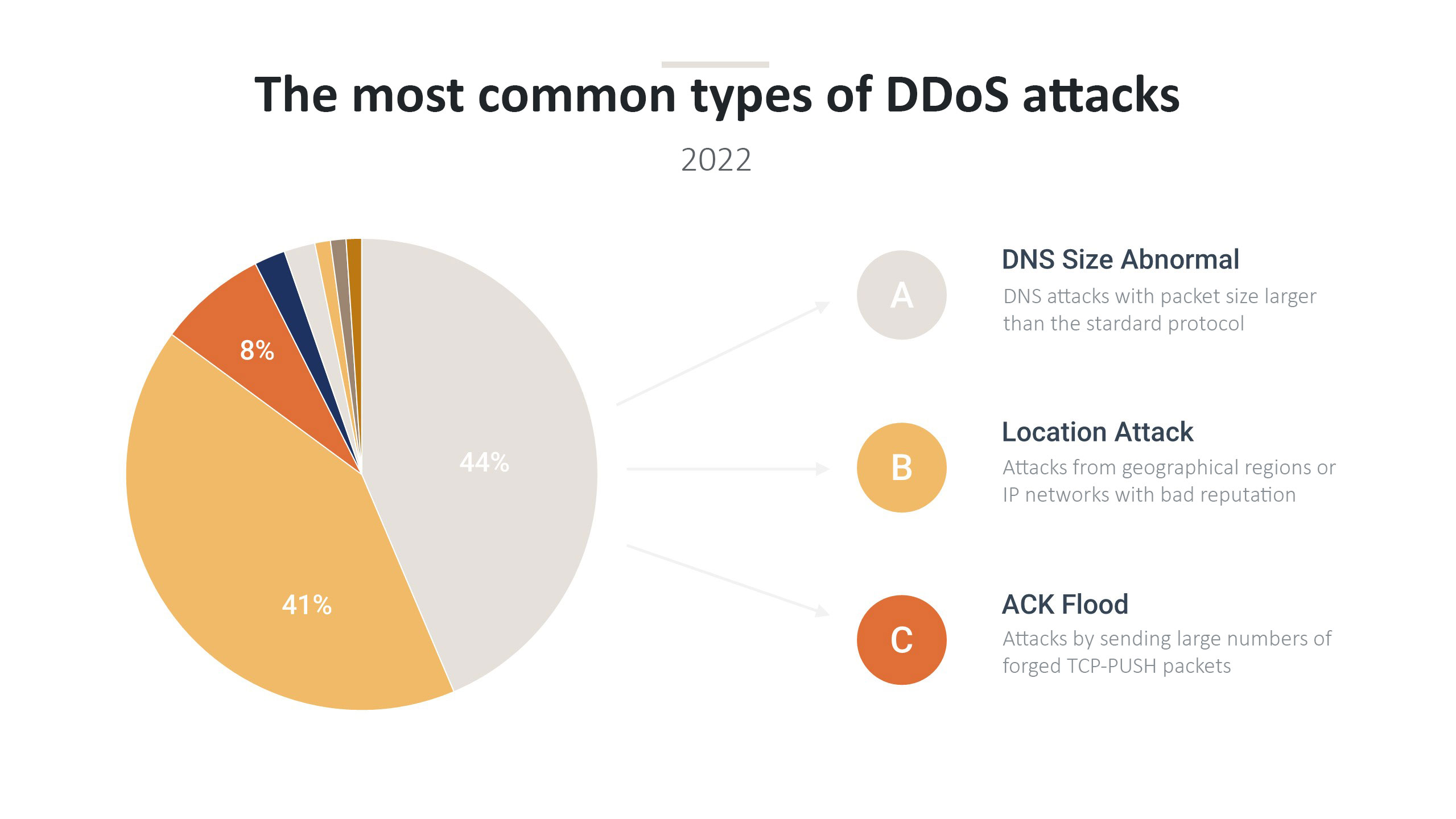
One of the significant trends observed this year is the constantly increasing number of intense DDoS attacks with a capacity of over 5Gbps.
There is also a growing trend of Amplification / Reflection attacks. Such attacks are performed whereas the perpetrators of the attack make requests to publicly available servers using the victim's IP address as the source identifier. In this way, the servers return a response to the real address of the final destination. The resources in question that "reflect" the requests of malicious users are most often "Domain Name", "Network Time Protocol" or WEB servers. This can be discovered when looking at the "source port" attribute of the Level 4 segment of the "Open Systems Interconnection" communication model. When we see a source port on UDP segment 53, it becomes clear that we are observing a DNS Amplification flood. The same applies to TCP port 21/80/443, from which we understand that FTP/HTTP/HTTPS communication protocols are used. TCP attacks can be of several types, with attackers typically taking advantage of the communication method and the various stages of the 3-way handshake required to establish a TCP session. Such type are SYN / ACK / SYN-ACK / FIN / RST flood.
We observe a growing number of multi-vector attacks as well. When attackers see that one type of attack is not working, they change their attack pattern and start using another type of servers for reflection or a different botnet network. Occasionally we observe several types of attacks using and/or targeting different resources at the same time. Evolink systems report a 70/30 ratio of Single-Vector / Multi-Vector attacks.
An interesting fact about "reflective" attacks is the resources that are used. In the first half of 2022 we observed a large number of attacks whose traffic mainly originates from "Universal Plug and Play (UPnP)" devices such as DVRs, cameras and printers. It is a good practice when using this type of equipment to change the standard ports for the management protocols and to configure a complex and long password with different characters and symbols.
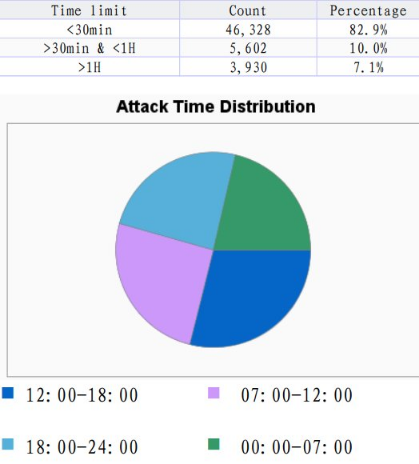
As can be seen in the statistics above, the most common duration of the attacks is under 30 minutes but attacks aiming to interrupt the connectivity of the end user for longer than an hour are also a significant share and should not be overlooked. The diagram on the other hand shows the time intervals during the day when malicious traffic is observed and as it indicates they are of equal values regardless of the time of the day.
Attempts to sabotage the network infrastructure before the end destination are increasing in number. Several devices are being attacked along the way to the end host, with the aim to overload the system resources of the network equipment and causing the victim to lose global network connectivity. Evolink advises following best practices for IP communication by configuring security policies where they are lacking.
Recommendations: